Inspirating Info About How To Check For Conficker Infection
Symptoms of a conficker infection include:
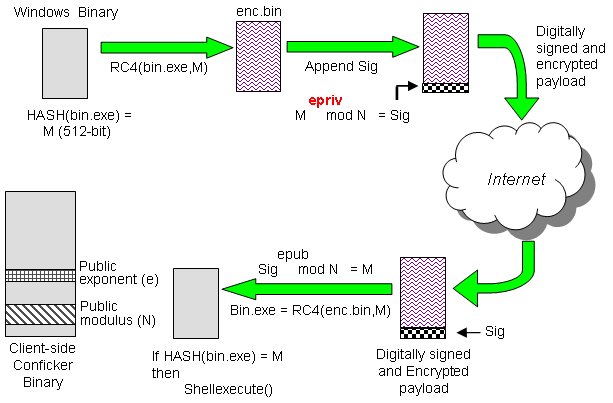
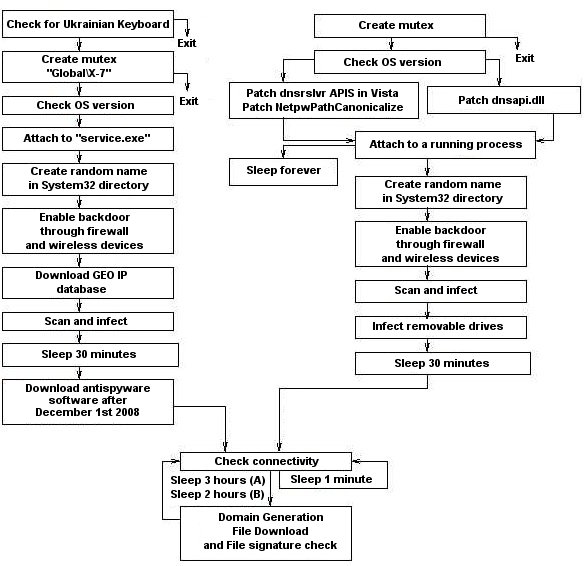
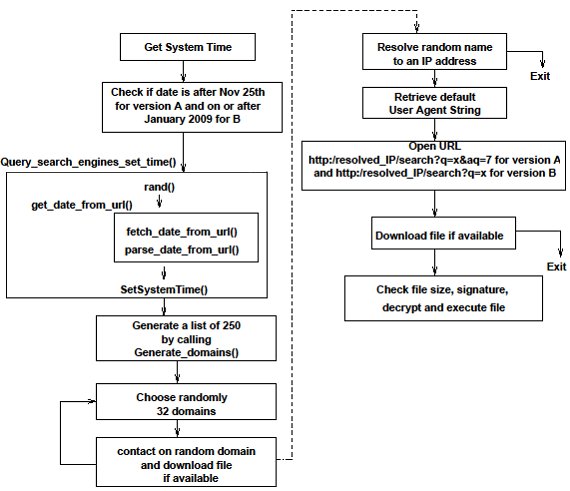
How to check for conficker infection. It will then send the ip. Ensure hips and buffer overflow. For example, you may want to check the date and time your av detected the worm on a specific machine and check the username that have been used (if available) at the time the.
If, on the other hand, any of the images are. Account lockout policies being reset automatically. Computer configuration\windows settings\security settings\file system.
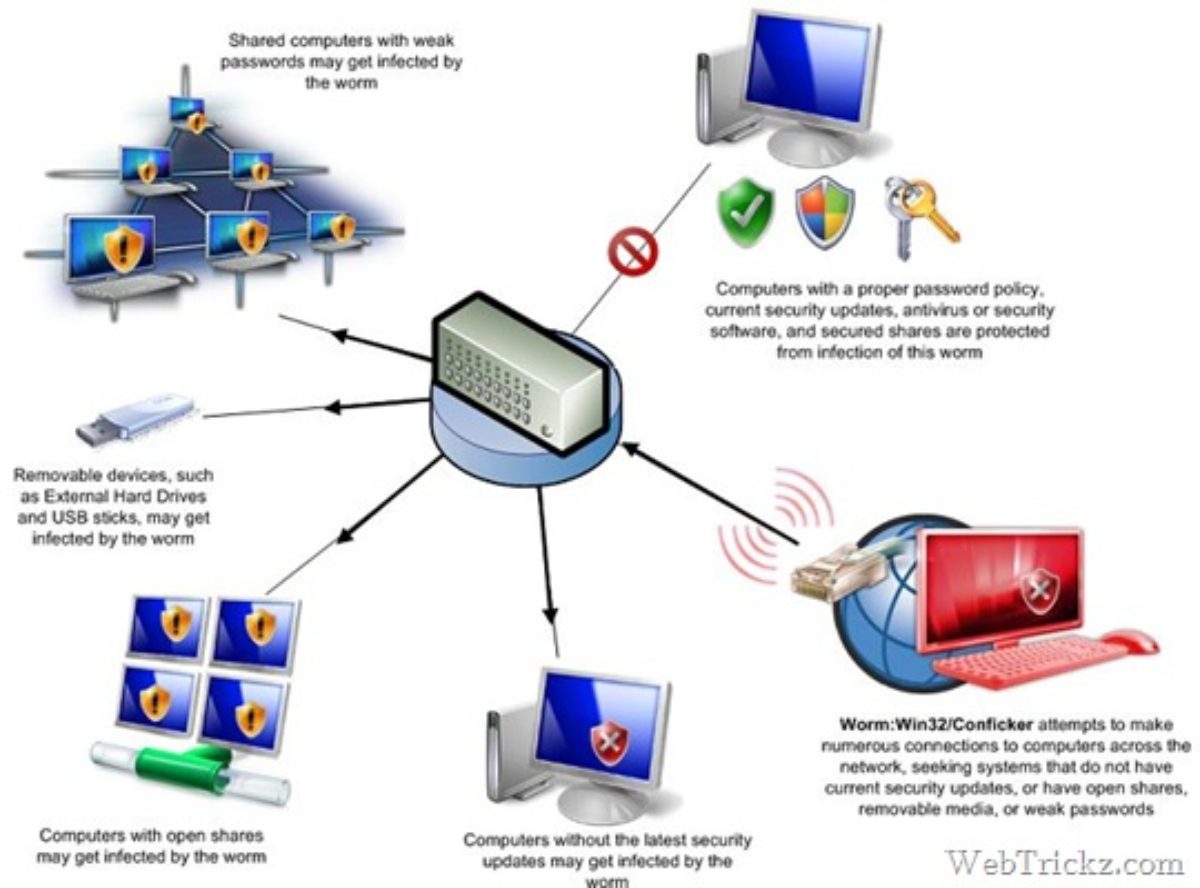
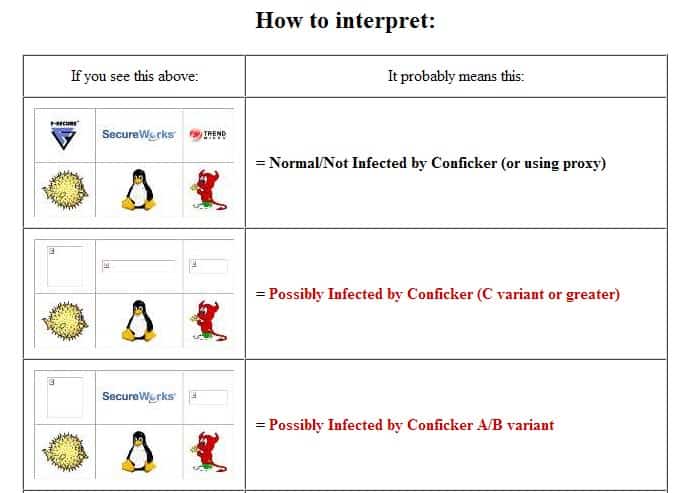
All you do is head to the conficker eye chart and check the table at the top. Ensure that all removable storage devices are scanned after being connected to a computer infected with the conficker family of worms. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.
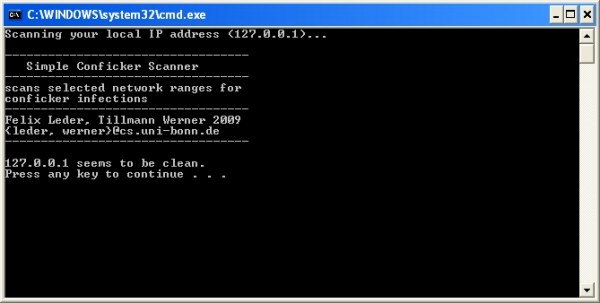
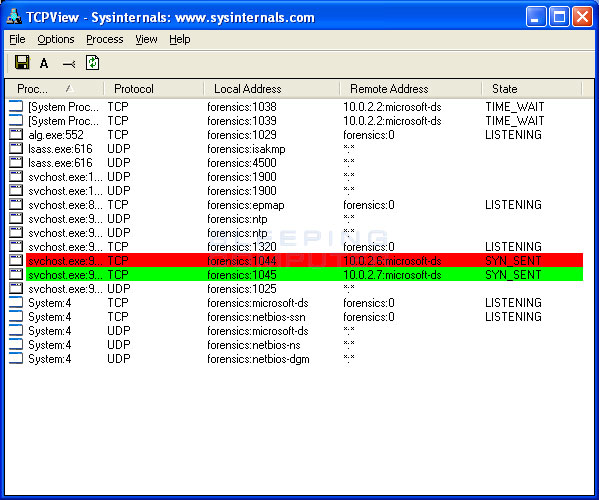
A quick visual scan can tell you whether you're infected with the conficker worm or similar malware. It connects to the following websites to check its own computer's ip address: Menu option as shown in the image below.
Certain microsoft windows services such as automatic updates, background intelligent. The conficker/downadup worm, which first surfaced in 2008, has infected thousands of business networks. Unpatched computers are most at risk of infection, with conficker exploiting these.
You need to understand the way that conficker operates to know where to look for it: The machine where conficker is running. If you see all six images, you're golden:









/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)


